Fun with Putty.
No...not silly putty. Putty - you know, the cool SSH client. I wanted to be able to log in to my Windows XP box at the house from work, but figure out how to do it securely with no weird holes in my firewall to open, etc. I also wanted to do it with free software. It was a success. Here's a brief rundown....
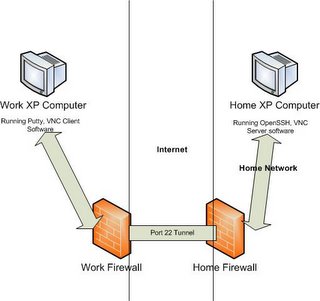
HOME COMPUTER STEPS.
1. Download the OpenSSH "SSHWindows - Installer" here. Install program using defaults.
2. Edit c:\program files\openssh\etc\sshd_conf file, uncommenting the line:
# AllowTcpForwarding yes
(Note: Uncommenting means to take the # sign out of the line, then saving the file. You can use notepad for this step)
3. Navigate to the c:\program files\openssh\bin directory.
4. Execute from the prompt the following, substituting a local user on your computer for the bracketed [USERNAME].
mkpasswd -l [USERNAME] >> ..\etc\passwd
5. Go to Control Panel>Administrative Tools>Services, and restart (or start) the service OpenSSHd. Change the properties so that it will start automatically.
6. Download RealVNC, TightVNC, UltraVNC, or you can use Remote Desktop, etc. For my example I used RealVNC, but many frown on its use because its not 'secure'. Well, we ARE going through a secure tunnel, so this is a moot point.
7. Install according to defaults, and choose a password. Make sure the VNC icon is in your system tray.
HOME FIREWALL STEPS.
1. This is going to be harder if you don't know how to use your firewall. The idea here is to forward all WAN traffic on your network on port 22 (SSH's tunnel port) to your Home PC's IP address. This will involve knowing your IP address, and knowing how to forward your port 22 traffic. This step is the same as if you would be running a WebServer from the house, except in that case, port 80 would be forwarded.
WORK COMPUTER STEPS.
1. Install RealVNC. (Or TightVNC, etc...) Take the defaults.
2. Install Putty. Note: Download the link that says "Windows-style installer (x86)". Take the defaults.
3. Create a new session, with the external IP address of your network. Note: Go to here from a computer on your home network to find out what your REAL IP address is.
4. Under the 'tunnels' section of the Putty configuration, add a local/destination port forward as follows:
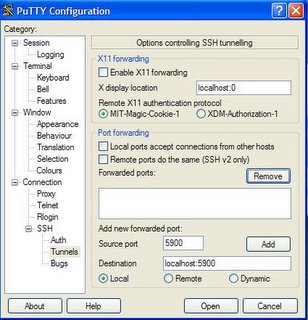
Click the 'Add' button. Make sure to save your session, back on the 'session' tree item.
5. Click 'Open' from Putty, and authenticate, using the user account you set up with OpenSSH. If the firewalls are configured, and OpenSSH is configured properly, you should be able to log in.
6. Open RealVNC on the work computer, and connect to "localhost:5900". Log in using the VNC password you set up on your home computer.
It took several tutorials on this process to get me through the whole setup. I was crucially missing the step to uncomment the 'AllowTcpForwarding' flag. Most tutorials skipped this step of the process.
This doesn't have to be just RealVNC applications. The port-forwarding principle is the same for any Internet protocol.

HOME COMPUTER STEPS.
1. Download the OpenSSH "SSHWindows - Installer" here. Install program using defaults.
2. Edit c:\program files\openssh\etc\sshd_conf file, uncommenting the line:
# AllowTcpForwarding yes
(Note: Uncommenting means to take the # sign out of the line, then saving the file. You can use notepad for this step)
3. Navigate to the c:\program files\openssh\bin directory.
4. Execute from the prompt the following, substituting a local user on your computer for the bracketed [USERNAME].
mkpasswd -l [USERNAME] >> ..\etc\passwd
5. Go to Control Panel>Administrative Tools>Services, and restart (or start) the service OpenSSHd. Change the properties so that it will start automatically.
6. Download RealVNC, TightVNC, UltraVNC, or you can use Remote Desktop, etc. For my example I used RealVNC, but many frown on its use because its not 'secure'. Well, we ARE going through a secure tunnel, so this is a moot point.
7. Install according to defaults, and choose a password. Make sure the VNC icon is in your system tray.
HOME FIREWALL STEPS.
1. This is going to be harder if you don't know how to use your firewall. The idea here is to forward all WAN traffic on your network on port 22 (SSH's tunnel port) to your Home PC's IP address. This will involve knowing your IP address, and knowing how to forward your port 22 traffic. This step is the same as if you would be running a WebServer from the house, except in that case, port 80 would be forwarded.
WORK COMPUTER STEPS.
1. Install RealVNC. (Or TightVNC, etc...) Take the defaults.
2. Install Putty. Note: Download the link that says "Windows-style installer (x86)". Take the defaults.
3. Create a new session, with the external IP address of your network. Note: Go to here from a computer on your home network to find out what your REAL IP address is.
4. Under the 'tunnels' section of the Putty configuration, add a local/destination port forward as follows:

Click the 'Add' button. Make sure to save your session, back on the 'session' tree item.
5. Click 'Open' from Putty, and authenticate, using the user account you set up with OpenSSH. If the firewalls are configured, and OpenSSH is configured properly, you should be able to log in.
6. Open RealVNC on the work computer, and connect to "localhost:5900". Log in using the VNC password you set up on your home computer.
It took several tutorials on this process to get me through the whole setup. I was crucially missing the step to uncomment the 'AllowTcpForwarding' flag. Most tutorials skipped this step of the process.
This doesn't have to be just RealVNC applications. The port-forwarding principle is the same for any Internet protocol.

0 Comments:
Post a Comment
<< Home